As companies rely more on cloud tools, managing logins has become a growing challenge. Single sign-on (SSO) provides a smarter way to balance convenience and security, all through one secure authentication system. The case for using SSO Most employees are drowning in passwords. Email, project management tools, HR portals, cloud storage, accounting platforms — the […]
Blog
How to keep your healthcare practice compliant with HIPAA

Protecting sensitive information is the core purpose of the Health Insurance Portability and Accountability Act (HIPAA). HIPAA mandates that patients have full control over access to their health records. Compliance is a strict requirement for any healthcare practice or business partner. To stay on the right side of the law, you need to pay close […]
What you need to know about the multifactor authentication vulnerabilities

Multifactor authentication (MFA) is widely used to secure online accounts, but it’s not without its flaws. While MFA adds an important layer of defense, it can still be bypassed by savvy cybercriminals. Understanding how attackers can exploit vulnerabilities is essential in improving your overall security. How cybercriminals can bypass MFA There are three main ways […]
Why Microsoft Whiteboard is becoming a go-to tool for team collaboration

With remote and hybrid work now the norm, visual collaboration tools have become essential for allowing teams to brainstorm, plan, and innovate together in real time. Learn how Microsoft Whiteboard helps distributed teams stay aligned, creative, and productive, no matter where they work. What is Microsoft Whiteboard? Microsoft Whiteboard is a shared digital workspace that […]
Why people are leaving your website early and how to hook them

You invest heavily in getting your name out there, but the calls just aren’t coming in. You don’t need to immediately blame your prices or what you sell; your site might be the real reason people are not buying. Small friction points, such as hard-to-read text or confusing menus, often cause potential customers to give […]
Cybersecurity for businesses: A simple defense plan for data loss

Data protection can be tricky. While most businesses know it’s important, few have the tools or knowledge to effectively secure their information. We’ve broken down key strategies to help you safeguard your business against data loss. Restrict access privileges to those who need it Access control defines who can view, change, or share information inside […]
The 2026 cybersecurity forecast: Threats and priorities

Drawing on their experience, cybersecurity experts Rob Wright (Dark Reading), David Jones (Cybersecurity Dive), and Alissa Irei (TechTarget) identified emerging threats and strategies businesses can use to build stronger defenses. Here’s a closer look at the trends they highlighted and what organizations can do to stay ahead. The evolution of AI-driven threats: Securing autonomous systems […]
Google Maps + Android XR is the future of hands-free navigation
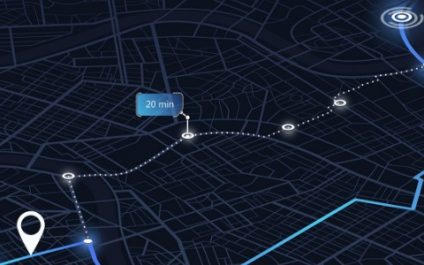
Forget fumbling with your phone for directions. Google’s Android XR platform and Gemini AI could soon bring enhanced Google Maps navigation to smart glasses, providing users with real-time, visual guidance while walking, complete with AI-powered corrections if they wander off route. Imagine walking through an unfamiliar city, unsure of which way to turn, until your […]
Why skipping iOS 26 could put your iPhone at serious risk

If you haven’t updated to iOS 26, your iPhone may be vulnerable to spyware attacks. Apple is sounding the alarm, but most users are ignoring it. Find out why delaying this critical patch is a dangerous gamble and what is fueling the widespread resistance to the latest update. Update lag leaves millions exposed Although iOS […]
Why Snapdragon PCs are first in line for Windows 11’s new update

Microsoft is rolling out Windows 11 26H1 to Snapdragon devices only, leaving Intel and AMD systems temporarily out of the loop. This isn’t about exclusivity but strategy. Why is Microsoft prioritizing Snapdragon devices? For businesses and IT leaders evaluating Windows 11 roadmaps and AI-ready hardware, this shift signals where Microsoft is placing its near-term priorities. […]

